E Mail Scanning Project
Project Objective
This aim of the project is to build an e mail scanning project that will be able to scan e mails to weed out suspicious e – mails for review by an administrator. This program will be able to scan e mail content for keywords that could indicate harmful intent such as terror, explosion, explosive, etc. Since modern day slang language uses many such words (Eg. Yesterday the store made a killing. We had over 300 customers!!), it is therefore necessary to set different weight age for different words and calculate a suspicion percentage calculated by finding sum of the weight age assigned to a word multiplied by the number of times the word is repeated divided by the total number of words in the email.
Emails that exceed a certain suspicion percentage will be tagged and sent to the administrator for review. The administrator will then be able to check the IP address for the sender and resolve the matter.
E Mail Scanning Snapshot
Existing Situation
In the current situation it is not possible to check every email send on the server for suspicious activity. An administrator would have to establish reasonable doubt and information so as to know which emails to target for checking. Thus the failure of the existing system hinges upon the sheer volume of emails sent in a system. Any person trying to avoid scrutiny simply needs to ensure that the email server has enough volume of email movement so as to reduce the probability of an administrator checking the email.
Proposed System
The proposed system will ensure that all emails passing through the server is scanned based on criteria set by the administrator. The administrator has to ensure that the database of words scanned and the weightage assigned to each word is updated. The administrator does not have to hunt for a needle in a haystack rather can use the immense computer resources available to make the task simpler. Upon notification of suspicious emails the administrator can take further action such as identification of sender, assessment of the situation and notification to relevant authorities on a case by case basis.
E Mail Scanning Modules
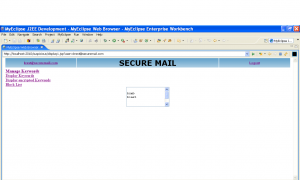
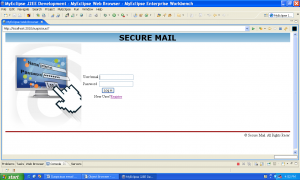
Login: This module is used to authenticate users and admin for further access to the mail system.
New user: First time users will create a login and email id through this module. The admin will have to approve the same and new users will be notified about the code of conduct within the mail system. The necessary disclaimers about the e – mail scanning system will also have to be accepted on this page.
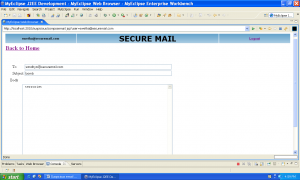
User: This is where a generic user can access the system for sending and receiving e – mails. Every access will log the IP address and login ID in a system for review by the administrator.
Scanner: This module is used when an e – mail is sent or received. The e – mail is scanned and a suspicion percentage is created for each e – mail. E – mails that cross a certain percentage will be automatically routed to the admin.
Admin: The admin will be responsible for updating the word list for the scanner and for taking further action on suspicious e – mails. The admin will be able to see login times, IDs and IP addresses for each login by users on the mail server.
Software Requirements
- Windows XP
- Apache Tomcat Web Server
- Oracle
Technology Used
- Java
- J2EE
Hardware Requirements
- Hard Disk – 2 GB
- RAM – 1 GB
- Processor – Dual Core or Above
- Mouse
Download Project
| Abstract Download | Download Abstract |
| E Mail Scanning Report | Download Project Report |

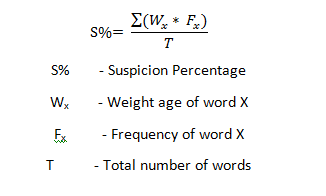

Leave a Reply